ALLOut Security Tips & Tricks for JD Edwards
 ALLOut Security Tips & Tricks for JD Edwards
ALLOut Security Tips & Tricks for JD Edwards
Brian Connor - Security Practice Manager
JDE security is the backbone of your users’ experience. The ability to make necessary changes quickly and easily can be the difference between a happy end user or a grumpy end user. However, there are shortcuts you can use to your advantage to make the management of your JDE security environment easier. We will look at a few tips and tricks using ALLOut Security, a third-party security provider.
Let’s start with setting up security for a new role. In standard JDE, it is very easy to copy the security setup from 1 role to another, but you can also copy the security from multiple roles into 1 role, and only retain the additional security granted. For this exercise, you will still need to create the JDE role in P0092 and assign the environments. Once that is done, you can go into P00950 and selecting the Form Exit Copy Security, you are given the option to copy the security from 1 role to another. When done with the copy and add option, only new security records are added to the role. If you are creating a new role that is a merge of 2 or more other roles, this is the way to go rather than exporting out to excel or copying individual lines. Even easier is using this ALLOut Security tip, use AOS Copy role function. With this tool, you can create a copy of an existing role, including creating the role (P0092), copying the same environments, security, role relationships, and even Finecut as the source role, all in just 1 click. If you already have most of the role created and you just want to copy some of the security, AOS allows you to copy security from a role to a user, from a user to a role, or user to user and role to role. You can copy all security, or just the security types that you want, like Action and Hyper exit security only.
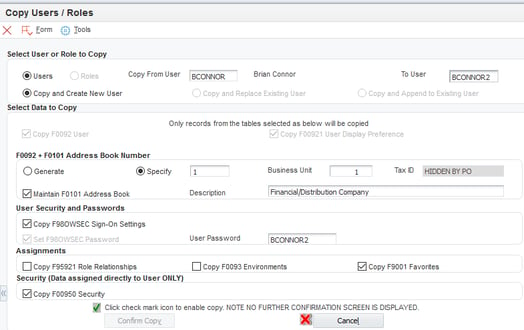
Looking at copying, or setting up new users? While standard JDE does allow you to copy a user to make a new profile, it is limited in what you can do. The profile basics are copied, but not much else. Using AOS, you can easily copy all aspects of the user, including creating the Address Book record (including business unit and Tax ID if needed), Role Relationships, Environments, Sign on security (P98OWSEC), User Display preferences, and even Favorites! Looking at the processing options for this AOS program, you can also define several default options to ensure new user accounts meet your security standards. Options here include setting the default password change frequency, allowed attempts, default password, and force password change on login. Need to setup a lot of new users? AOS has you covered here as well. You can gather the user information in a spreadsheet and upload to JDE using the user maintenance grid, or just type it in one at a time. Either way, you will save hours over using the P0092 interface.
Are you curious about what users you have in the system that do not have any roles assigned, or roles that are not assigned to users? Using the AOS System Workbench, you can get a high-level view of all of your users and roles in one place. The unique QBE interface allows you to search for both positive and negative values. For example, using the QBE, you can search for roles that are assigned to users, but do not have environments assigned. In addition, you can easily see if the role has Finecut, and the types of security applied within the role. This handy tool gives you a unique insight into data that would otherwise require some fancy SQL queries across multiple tables and does it in a very easy to see format in real time.
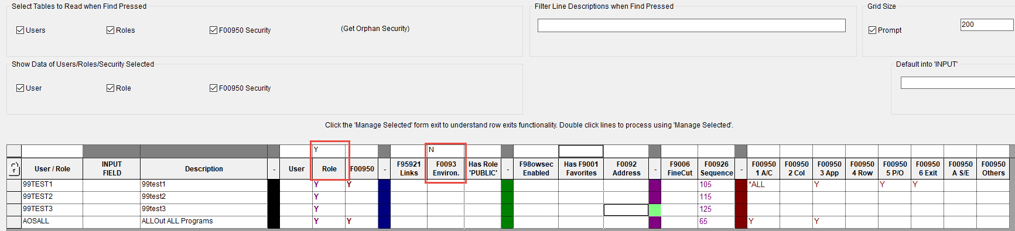
Still using this tool, it is a simple exercise to add environments to multiple users or roles all at once. You can also Finecut entire TaskViews for multiple roles, with a couple clicks of your mouse.
I saved my favorite tip for last! If you have ever worked with me, you know that one of my go-to programs for ALLOut Security is the 3-way match. No, not the financial one, but the AOS 3WM. This amazing tool gives you an easy way to troubleshoot user access issues, identify the roles that have visibility to a particular part of the TaskView, and even see the programs and UBEs available as exits from a program AND also see the access your user has to those exit programs and so much more! One of my favorite parts of this program is the ability to put in a user profile, and have the program load the active roles for the user, load what the user can see on the TaskView, and then display the level of access for each object that is visible. If I find an exit program that was overlooked during the security setup, it is a couple of mouse clicks to grant a role access to the program in the same screen.
If you would like to discuss your JDE security situation to review best practices and to see the AOS tips and tricks in action on your JDE system, contact our security practice today!
CONTACT US TODAY
FOR MORE INFORMATION ON GSI'S JD EDWARDS SECURITY SERVICES
